The National Cybersecurity Protection System (NCPS) is a holistic and unified strategy designed to protect the information technology infrastructure of Federal Civilian Executive Branch (FCEB) agencies. By providing a range of capabilities—such as intrusion detection, advanced analytics, and efficient information sharing—NCPS establishes a solid technological foundation that enables the Cybersecurity and Infrastructure Security Agency (CISA) to combat ever-evolving cyber threats effectively.
Essential Elements of NCPS
At its foundation, NCPS includes a wide array of components such as hardware, software, supporting processes, training initiatives, and various services. These elements are carefully acquired, engineered, and maintained to support the agency’s comprehensive cybersecurity mission. A key highlight of the NCPS framework is EINSTEIN, an advanced intrusion detection system. EINSTEIN plays a vital role in defending federal networks by offering an early warning mechanism, improving situational awareness around intrusion threats, and enabling near real-time detection of malicious cyber activities.
Working Together to Develop Capabilities
The success of NCPS relies heavily on strong collaboration and integration with a variety of federal partners. This cooperative strategy is crucial for bolstering the defense capabilities of their networks. By nurturing these relationships, CISA can create and provide analytical tools and real-time defensive services that significantly strengthen the security of FCEB networks. This teamwork produces vital insights into cyber incidents and fosters situational awareness, which is essential for incident response teams, government agencies, critical infrastructure entities, and national leadership.
Mechanism for Detecting Intrusions
The Intrusion Detection capability of NCPS, provided through the EINSTEIN system, operates as a sensor grid that constantly tracks network traffic for indicators of malicious activity directed at participating departments and agencies (D/As). This advanced system employs signature-based intrusion detection technology to detect potentially harmful traffic entering or exiting federal networks. Consequently, CISA cybersecurity analysts obtain a clearer view of the network landscape, enabling them to identify vulnerabilities and effectively address weaknesses.
Protecting Cybersecurity Privacy
CISA prioritizes the integration of privacy protections across all its initiatives from the outset. This comprehensive approach to privacy oversight includes the involvement of the Chief Privacy Officer and dedicated privacy personnel throughout the agency. For every CISA project, Privacy Impact Assessments (PIAs) are conducted to identify and address potential privacy risks throughout the development lifecycle. These assessments clarify for the public what personally identifiable information (PII) is collected, the rationale behind its collection, and how it will be utilized, shared, accessed, and stored. By following the Fair Information Practice Principles, PIAs are essential in reducing any adverse effects on individual privacy. The Department of Homeland Security (DHS) has also performed a PIA specifically for the NCPS, establishing a framework for addressing privacy concerns.
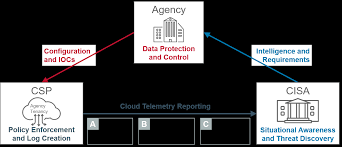
Moving in the Direction of Cloud Security
As the cybersecurity landscape continues to change, CISA’s Cybersecurity Division (CSD) is evolving to ensure effective capture and analysis of security information related to cloud-based traffic. This shift allows CISA analysts to maintain situational awareness and provide ongoing support to federal agencies as they address the challenges of cloud security. To achieve this, CISA is creating a cloud-based architecture specifically designed to gather and analyze security data from agency cloud environments.
Reference Architecture for the NCPS Cloud Interface (NCIRA)
The NCPS Cloud Interface Reference Architecture (NCIRA) is divided into two volumes that serve as a resource for agencies on how to engage with the cloud-based system. The first volume outlines the enhancements that the Cybersecurity Division (CSD) is making to improve the collection of relevant data from agency cloud environments, as well as general reporting patterns for sending cloud telemetry to CISA. The second volume provides an index of typical reporting patterns and offers guidelines for how agencies can transmit cloud-specific data to the NCPS architecture.
Cloud service providers can refer to both Volume One and Volume Two of the NCIRA to ensure that their solutions align with the established reporting standards, promoting effective management of cloud security data.
Conclusion
The National Cybersecurity Protection System (NCPS) plays a crucial role in bolstering the cybersecurity framework for federal agencies. By utilizing cutting-edge technologies like EINSTEIN and promoting collaboration among various stakeholders, CISA significantly enhances its ability to detect and respond to cyber threats. As the digital landscape evolves—especially with the increasing prominence of cloud computing—the NCPS is adapting to meet these new challenges and protect critical information infrastructure. Through continuous development and strategic partnerships, the NCPS serves as a formidable defense against the rising tide of cyber threats, ensuring the integrity and security of federal information systems.














Leave a Reply